Which Method Is Used to Check the Integrity of Data
The hash of a hashing algorithm used for integrity validation is often called a checksum and is appended at the end of the data to be transferred. Which statement describes cyber warfare.
A trigger is an event driven procedure attached to a database table.

. Data integrity is enforced by database constraints. Which method is used to check the integrity of data. The CRC technique is used to protect blocks of data called frames.
Make political statements or create fear by causing physical or psychological damage to victims. You can send a PUT request to upload an object of up to 5 GB in a single operation. CRC Cyclic Redundancy Check CRC is a powerful and easily implemented technique to obtain data reliability in network transmissions.
With a backup the recovery and restoration of missing data files can take place more smoothly helping to preserve the data integrity of restored records. You can send REST requests to upload an object with a checksum value to verify the integrity of the data with PutObject. This question was created from Quiz 1docx.
You can also retrieve the checksum value for objects using GetObject or HeadObject. Engineering Technology Computer Science. What tools you use to enforce the data integrity depend on your system requirements.
We also achieve this in a manner in which a digital proof stamp can be made visual to help achieve virality for the end users. They can be used to check the integrity whenever data is entered into it. Check for data consistency.
Chapter 1 Quiz Answers ITC 212 1. Methods including data encryption username ID and password and two factor authentication can be used to help ensure confidentiality of information. File permission control version control and backup are methods that can be used to help ensure integrity of information.
Integrity checkers also provide the only reliable way to discover what damage. We at BugRaptors during the testing of Data integrity enforcement makes sure that Data integrity is enforced by features such as check constraints triggers views stored procedures user-defined functions andor referential constraints. An integrity check program with built-in intelligence is the only solution that can handle all the threats to your data as well as viruses.
Comments 0 Answer. We also achieve this in a manner in which a digital proof stamp can be made visual to help achieve virality for the end users. ETC Source and Data Integrating Test This test is used to examine most of the tests and evaluate most Data Integrity.
This research outlines a method in which integrity authentication and provenance can be established for raw data within a file even when the metadata attached to it has changed. Which method is used to check the integrity of data. Choose three something you know.
The common methods used for data integrity check include. Integrity checking products work by reading your entire disk and recording integrity data that acts as a signature for the files and system sectors. Also used to verify all valid invalid conditions then subsequently we proceed for source and targeted data.
This is the case for barcodes ISBN numbers and credit card numbers where the last digit of the code is a check digit the. Characteristics of Data Integrity Testing. Which method is used to check the integrity of data.
Checksum backup authentication encryption A checksum value of a block of data is calculated and transmitted with the data. This can be employed by network storage systems to detect integrity violations in data transmissions across nodes. Error checking and validation for example are common methods for ensuring data integrity as part of a process.
High availability systems typically include these three design principles. Methods including data encryption username ID and password and two factor authentication can be used to help ensure confidentiality of information. It can describe the state of your dataeg valid or invalidor the process of ensuring and preserving the validity and accuracy of data.
Data integrity testing verifies that the data in the database is accurate and functions as expected within a given application. File permission control version control and backup are methods that can be used to help ensure integrity of information. We also perform data integrity testing by keeping in mind all the positive and negative scenarios in order to cover all the.
Validating each value if it is successfully saved to the database. It is Internet-based conflict that involves the penetration of information systems of other nations. The term is broad in scope and may have widely different meanings depending on the specific context even under the same general umbrella of.
For the purpose of authentication what three methods are used to verify identity. This research outlines a method in which integrity authentication and provenance can be established for raw data within a file even when the metadata attached to it has changed. Here are some of the best practices of data integrity that can minimize or eliminate the risks of data breaches in a database.
Limit access to data and change permissions to constrain modifications to data by unapproved parties. They include the following 7 constraint types. Detect failures as they occur.
Which method is used to check the integrity of data. We suggest a data backup and restoration plan to be implemented in the event of a device failure program error or data erasure. Data integrity is the maintenance of and the assurance of data accuracy and consistency over its entire life-cycle and is a critical aspect to the design implementation and usage of any system that stores processes or retrieves data.
After the data is received the checksum hashing is performed again. The logic here is implemented by using our own user-defined data integrity. Checking whether or NOT a blank value or default value can be retrieved from the database.
It focuses on-Check foreign primary key integrity. Checks test correctness of data transformation. Data Integrity testing involves.
Sometimes the hash is called a check digit if it only consists of one digit. Database Constraints are declarative integrity rules of defining table structures. The calculated value is compared with the transmitted value to verify the.

This Article Gives You An Overview On Sql Server Database Integrity Check Sql Server Sql Server
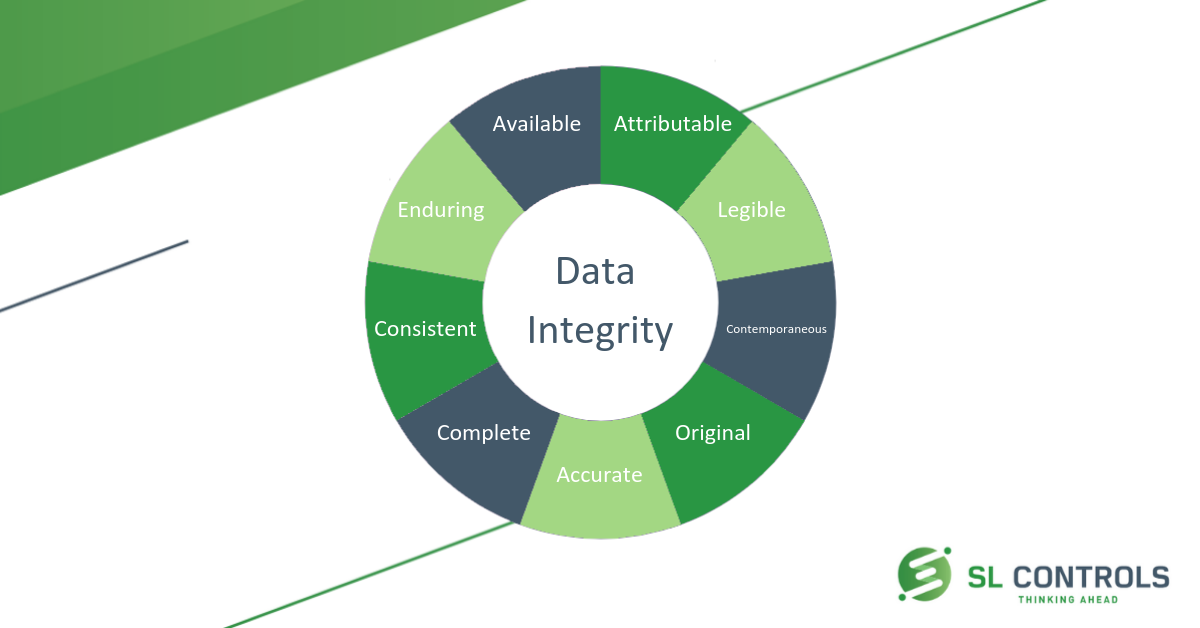
What Is Alcoa And Why Is It Important To Validation And Data Integrity Sl Controls

Comments
Post a Comment